This topic is helpful for customers who use Powerlynx and Splynx at the same time and want to configure the same MikroTik NAS device to work with both platforms simultaneously.
Warning: You should ensure that your device has enough resources and can properly handle multiple types of connections before implementing this configuration.
Moreover, you must be aware that it’s easy to set up an incorrect configuration, which can cause multiple network issues for both you and your customers.
If you’re confident that this setup is feasible in your environment, here are a few practical recommendations to help you build a stable and functional system.
1. VPN Configuration
This is one of the most essential steps. A correct VPN configuration helps avoid potential issues like misrouted packets and RADIUS server communication failures.
Both Powerlynx and Splynx allow you to establish VPN connections (WireGuard or OpenVPN) with your MikroTik NAS. However, there’s a key difference:
- Powerlynx does not allow customization of the WireGuard or OpenVPN subnets—it uses fixed internal IP ranges.
- Splynx allows you to change the internal VPN subnets.
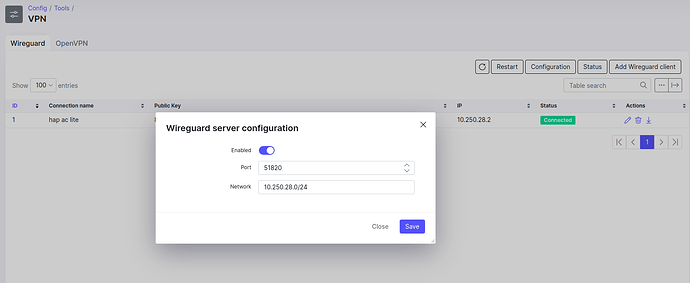
So, when using both services on the same router, it’s important to assign different subnets and possibly different ports for each VPN connection to avoid conflicts.
Powerlynx VPN Details
OpenVPN Configuration:
Powerlynx uses the 10.112.0.0/16 range for its OpenVPN tunnel.
| Attribute | Value |
|---|---|
| OpenVPN Server IP | 10.112.0.1 |
| RADIUS Server IP | 10.112.0.2 |
| OpenVPN Endpoint | openvpn.powerlynx.app:443 |
WireGuard Configuration:
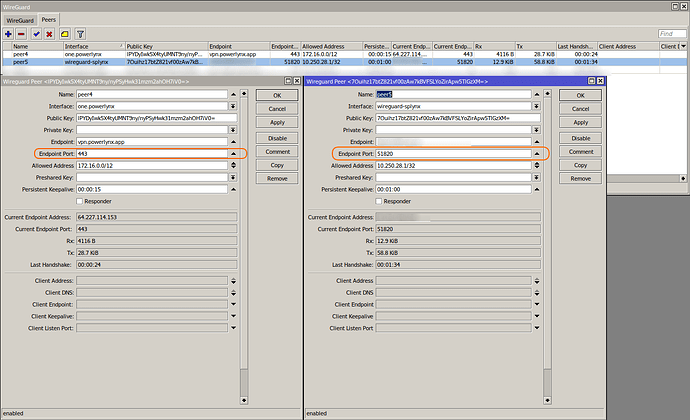
Powerlynx uses the 172.16.0.0/12 range for its WireGuard tunnel.
| Attribute | Value |
|---|---|
| RADIUS Server IP | 172.16.0.1 |
| WireGuard Endpoint | vpn.powerlynx.app:443 |
Splynx VPN Configuration
When setting up Splynx, make sure to choose VPN IP ranges different from those used by Powerlynx. For example, for WireGuard, do not use 172.16.0.0/12.
Additionally, Powerlynx uses port 443 for both OpenVPN and WireGuard, but in Splynx, you can configure different ports—such as the default 51820 for WireGuard.
You can configure Splynx VPN ports under:
Config > Tools > VPN > WireGuard > Configuration
Example Screenshots
Splynx WireGuard Settings
MikroTik WireGuard Endpoints
2. RADIUS Configuration
Different VPN IPs and routing rules help avoid packet misrouting, but you also need to be very careful with the RADIUS service settings on the MikroTik NAS.
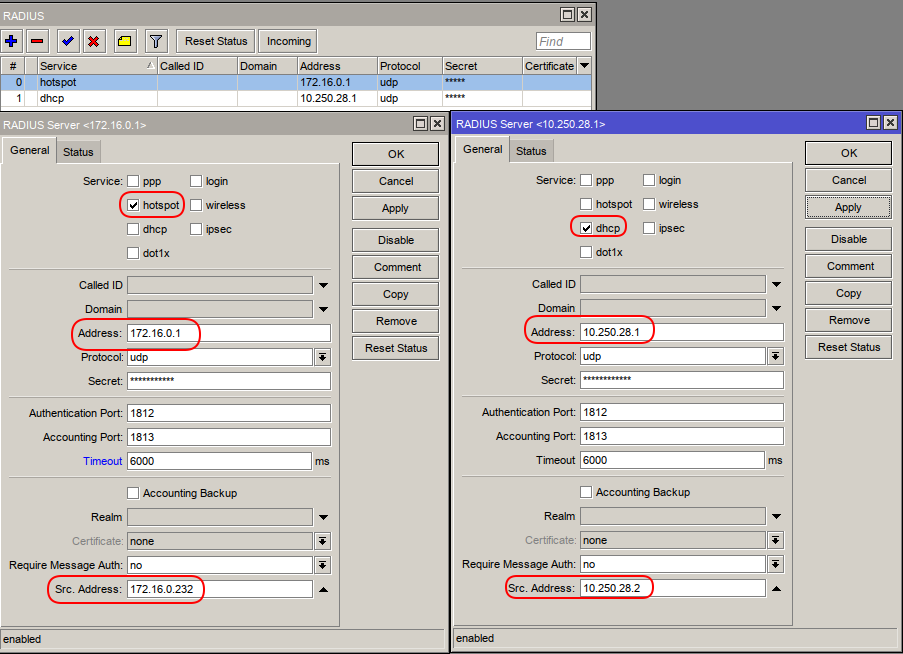
Important Note: RouterOS allows you to configure multiple RADIUS clients. However, if you assign the same service (e.g.,
hotspot) to multiple RADIUS servers, MikroTik will use the one with the lowest ID, while the others will be used as failovers.This means that if both Powerlynx and Splynx are configured to handle
hotspot, only one will actually receive requests—usually not the one you intended.
Best Practice
- For Powerlynx, set the service to
hotspotonly. - For Splynx, use other available services (such as
ppp,login, ordhcp) based on your actual deployment type.
This avoids traffic routing conflicts between the two RADIUS servers.
Example: MikroTik RADIUS Configuration
3. Firewall Configuration
Make sure your MikroTik firewall allows traffic to and from both Powerlynx and Splynx services.
If your router has active drop rules, you need to explicitly allow:
- VPN connections (WireGuard/OpenVPN)
- RADIUS server IPs
- Management IPs (if needed)
Refer to this detailed article for more help:
![]() Recommended MikroTik Firewall Configuration
Recommended MikroTik Firewall Configuration
4. Separate Interfaces for Powerlynx and Splynx
To prevent conflicts, do not use the same physical or virtual (VLAN) interfaces for both Splynx and Powerlynx client connections.
For example:
- If your hotspot users (managed by Powerlynx) are connected via bridge or VLAN1,
- Then configure your Splynx users (IPoE, DHCP, PPPoE, etc.) on a separate interface or VLAN.
This separation helps avoid ARP issues, DHCP conflicts, or queue mismatches.
You can also separate Powerlynx clients at Layer 2 using VLANs. More on this below: